With global cumulative investment in financial technology (fintech) forecast to exceed US$150 billion in three to five years, economies around the world are vying to attract fintech innovators and cash in on this growing industry. Singapore, too, has thrown down… Read More
Articles
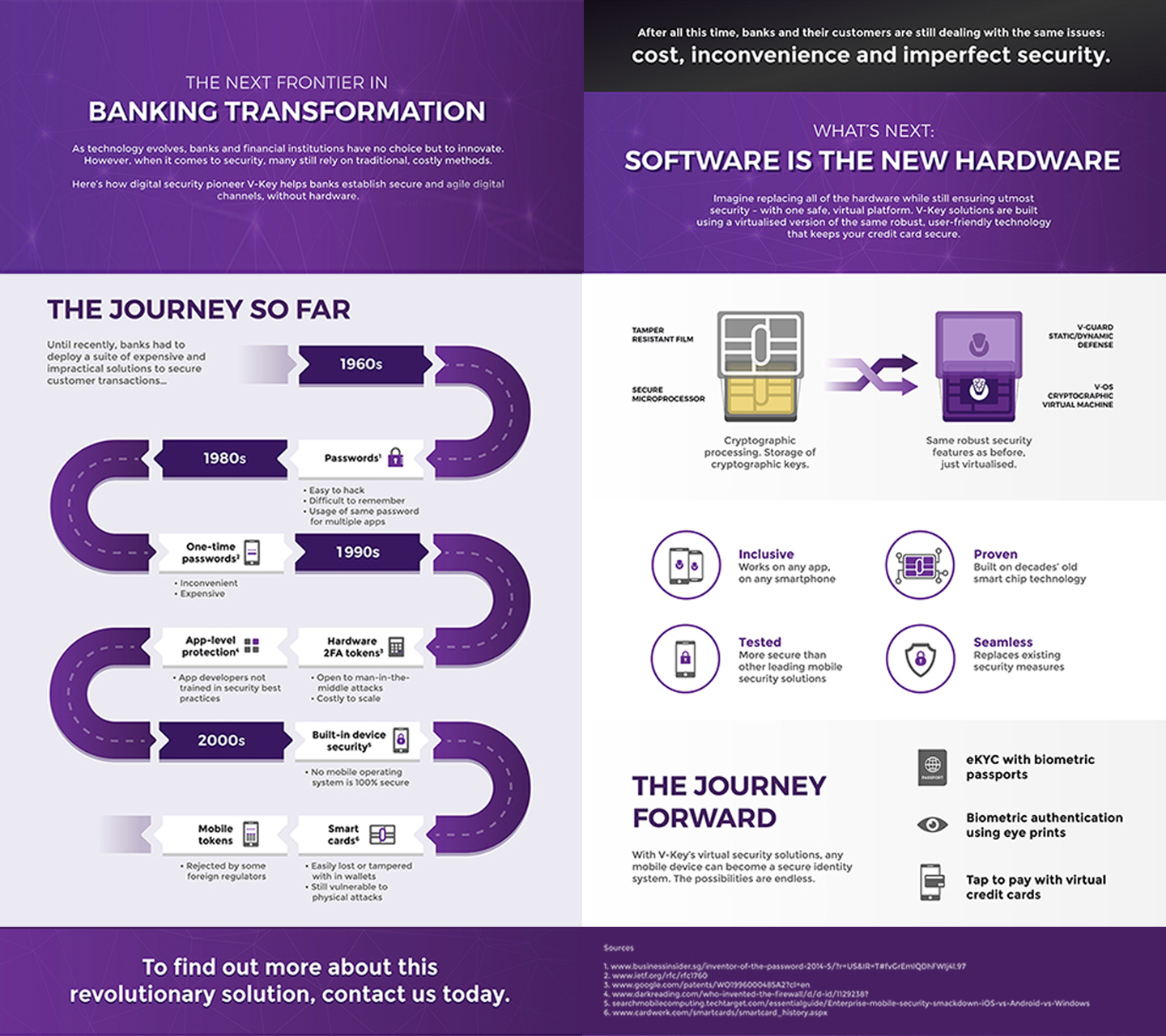
Infographic: The next frontier in Banking transformation
Here’s how digital security pioneer V-Key helps banks establish secure and agile digital channels, without hardware. As technology evolves, banks and financial institutions have no choice but to innovate. However, when it comes to security, many still rely on traditional,… Read More
Is software-based Biometrics Authentication the solution to ASEAN’s regulatory challenges?
Banks in Southeast Asia should look towards software-based biometrics as the way forward to navigate the regulatory differences in the region and secure their customers’ transactions. The ASEAN region is made up of 10 countries, with clear differences in their geography,… Read More
How does a Virtual Smart card protect a customer if they lose or change their mobile phone?
From banks to government agencies, many organisations are intrigued by and exploring software security solutions such as mobile tokens and mobile identity systems for individual identification, authorisation and authentication. This raises questions such as: What happens if a mobile banking customer… Read More
Building V-OS with HSM
V-OS is the world’s first virtual secure element, a software solution with security built into the firmware code. These include secret cryptographic parameters and data, which need to be randomly generated and securely persisted, and are then transformed into code… Read More
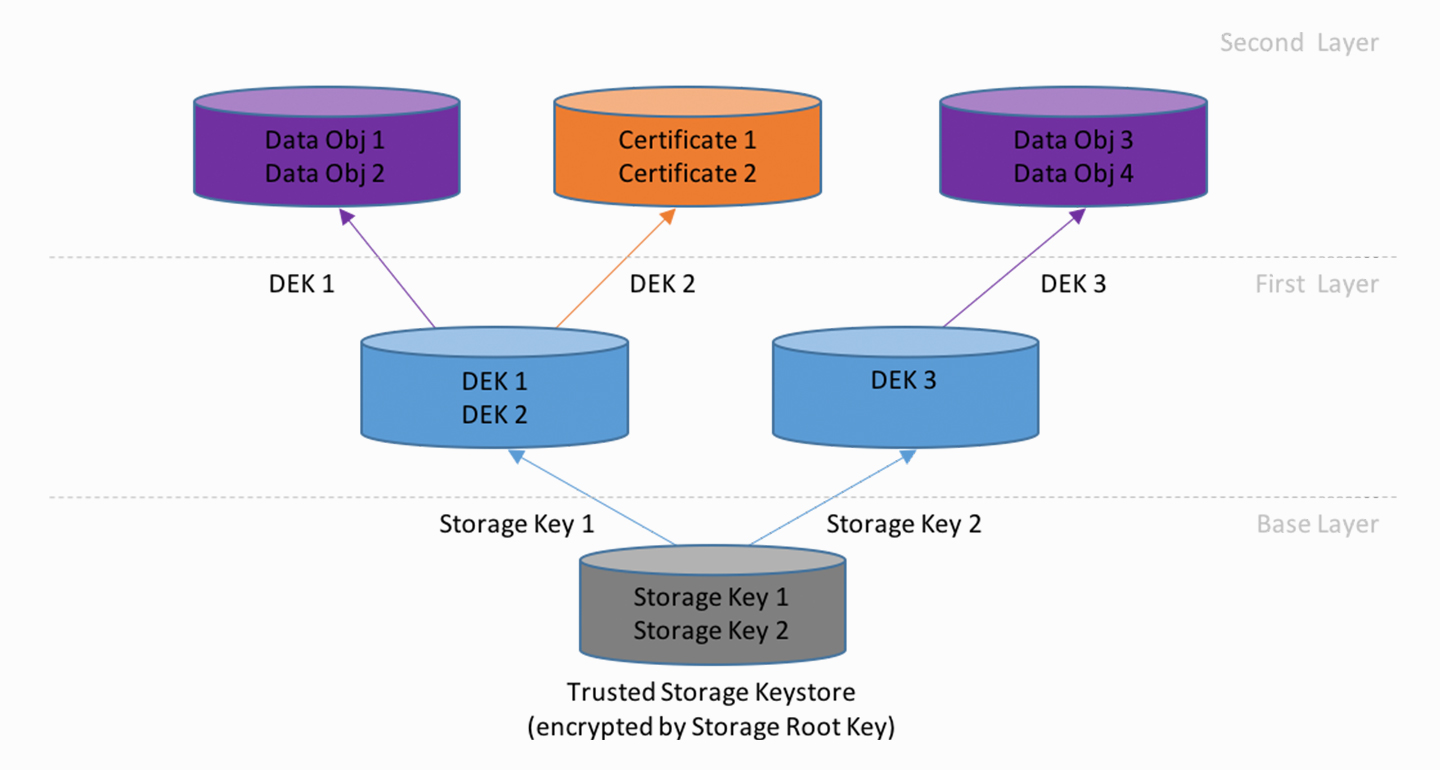
Cryptography in V-OS
V-OS is the world’s first virtual secure element. This is something we at V-Key take great pride in. It is also a claim we dare to make, based on the innovation that has gone into virtualizing the hardware tamper-proof protection, the… Read More

Why Existing Mobile Software Protections are Insufficient
Why Existing Mobile Software Protections are Insufficient In August 2018, Security researchers from Kryptowire, a security firm, found 38 different vulnerabilities loaded onto 25 Android phones, including devices from Asus, ZTE, LG and the Essential Phone, which are used by global… Read More

