For businesses, especially those handling sensitive data or financial transactions, ensuring app security is no longer optional. The risk is real: attacks on mobile apps can lead to reputational damage, regulatory fines, and the loss of user trust. V-OS App Shield… Read More
Articles

Securing Mobile Apps and Why It’s Critical for Businesses
Mobile devices continue to become indispensable, with the average smartphone user spending around 88% of their day interacting with apps. This surge in mobile usage highlights an escalating need for businesses to ensure their apps are secure, as the stakes… Read More

Introducing V-OS App Shield: Connect, Deploy and Protect your App in Minutes
Mobile applications are key to daily business operations, customer engagement, and overall functionality. According to Google, the average smartphone user interacting with nearly 10 apps daily and spending about 88% of their time on mobile, the need for strong mobile… Read More

V-Key partners with Bridge Alliance to build a Safer Digital Ecosystem
V-Key, renowned for its advanced security solutions has proudly joined Bridge Alliance as their technology Partner, solidifying their commitment to innovation and excellence in mobile security. This partnership opens doors to explore new avenues for enhancing authentication experiences and mitigating… Read More

Making 2FA/MFA robust against smishing and related attacks
Traditionally, authentication of users of web and mobile applications has been done with username/password logins. However, attackers soon found vulnerabilities that could be exploited. Users might use weak passwords, use the same password for multiple accounts, share passwords, etc.; even… Read More

How do we determine the effectiveness of mobile apps’ security systems?
How do we determine the effectiveness of mobile apps’ security systems? With the spate of remote working regime due to Coronavirus pandemic, the reliance and growth for video conferencing platform has been exponentially escalated. Zoom, one of the more widely and… Read More
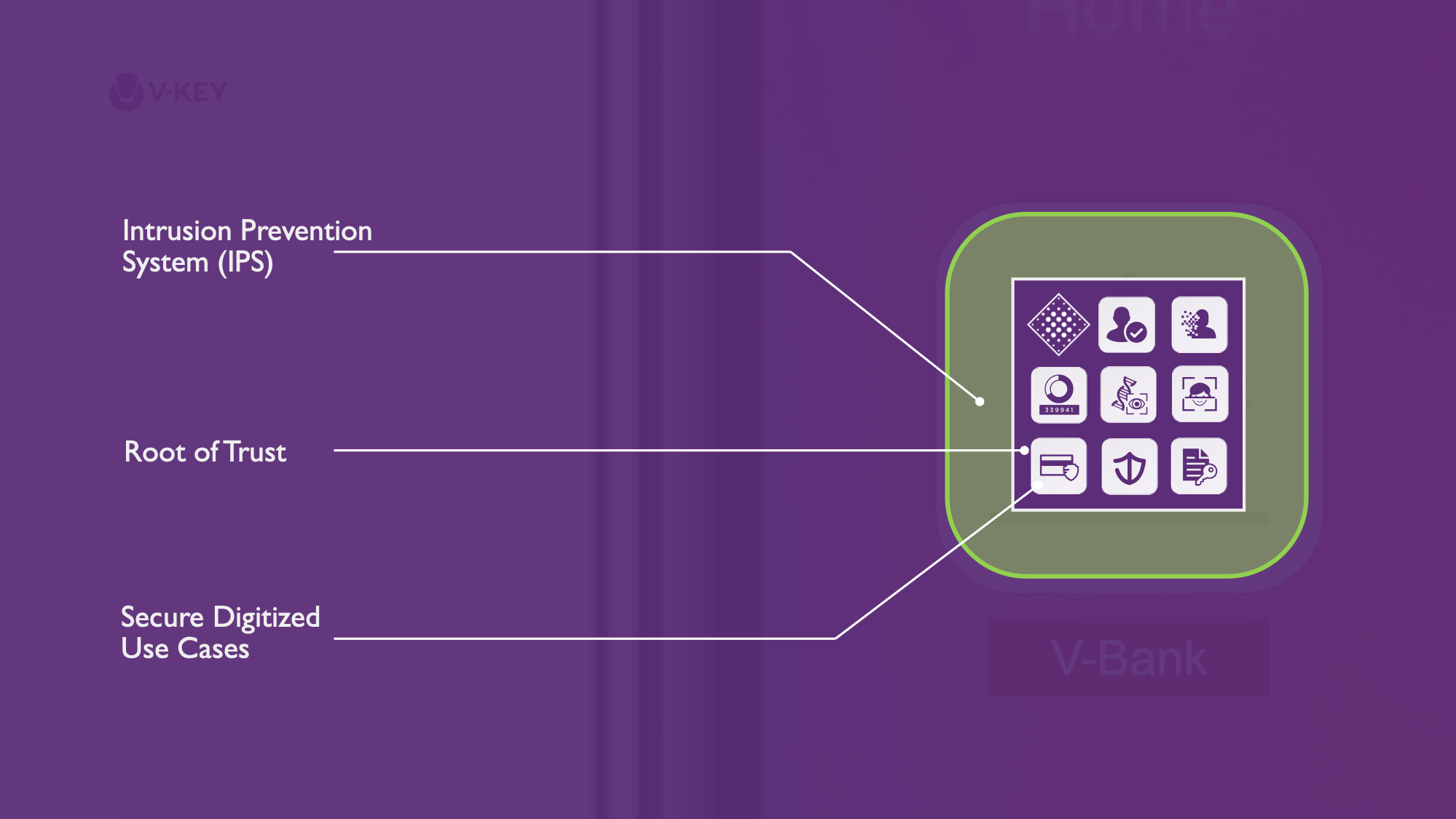
Is the detection of jailbroken/rooted phone sufficient against threats?
Is the detection of jailbroken/rooted phone sufficient against threats? It is widely known that performing jailbreaking/rooting opens the mobile device to security vulnerabilities. It often leaves a gap for malware to gain elevated permissions on a device. This elevated access allows… Read More
Three steps to fight the Mobile Security status quo
50 minutes per day. That’s the amount of time an average user spends on Facebook, Facebook Messenger, and Instagram. There are lots of reasons for the “stickiness” of these social networking apps, but a big part of their appeal is what… Read More
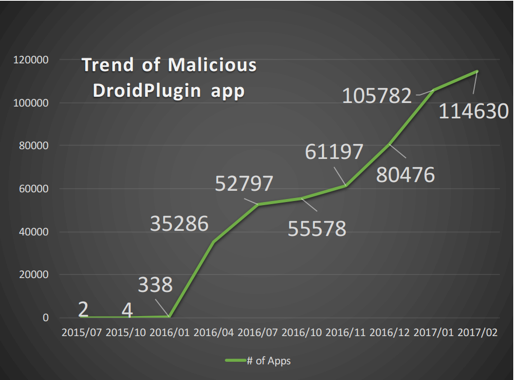
V-OS Protection against Android Plugin malware
V-OS Protection against Android Plugin malware There has been a recent surge in Android malware abusing Android Plugin Frameworks for malicious behavior. DroidPlugin, Parallel Space and VirtualApp are several plugin frameworks that have been abused by malware in recent months to… Read More
V-OS Protection against CPU vulnerabilities
Virtually every computing device in the world is made unsafe by the latest disclosures on Central Processing Unit (CPU) vulnerabilities. Overview of the CPU and its functions The CPU is most often described as the “brain” of any computing device. It is… Read More

