Fast builds. Secure releases. Zero code changes.
Mobile development moves fast. There are always new features to launch, bugs to fix, and deadlines to meet—and developers are expected to deliver quickly. That’s why security needs to move just as fast, without slowing anything down.
V-OS App Shield was built for that pace. It’s a no-code mobile app protection solution that secures your app without touching your source code or changing how your build process works.
Upload your signed APK or IPA to the web portal or integrate via API, and in minutes, you’ll get a hardened version of your app, protected against reverse engineering, tampering, and runtime threats. No SDKs. No configuration. Just silent, reliable protection built to scale with your development process.
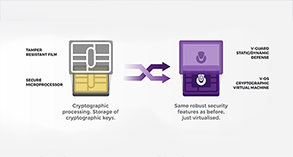
At the core of App Shield is V-OS, V-Key’s patented Virtual Secure Element. Unlike hardware-based protections like Secure Enclave or Trusted Execution Environments (TEE), V-OS is entirely software-based meaning it works reliably across all supported devices, platforms, and OS versions.
V-OS acts like a virtualized security core inside your app. It enables App Shield to inject runtime defenses directly into your binary providing protection that travels with your app, no matter where it runs. That includes anti-tampering, anti-debugging, root/jailbreak detection, and protection against runtime manipulation tools like Frida or Xposed. And because it’s virtual, there’s no dependency on specific device models or OEM support making it easier to scale protection without limitations.
What App Shield Protects Against
Mobile apps are increasingly targeted by attackers using sophisticated tools that don’t require physical access to devices. These aren’t theoretical risks they’re real, repeatable methods that exploit app-level weaknesses in the wild.
App Shield is designed to defend against:
- Reverse Engineering – Tools like JADX or Hopper can decompile apps to reveal logic, assets, or credentials.
- Runtime Manipulation – Frameworks like Frida and Xposed inject code on the fly to bypass checks or modify behavior.
- App Tampering and Repackaging – Malicious clones with injected malware are distributed to users as legitimate apps.
- Emulator and Root-based Attacks – Fake environments and rooted devices are used to spoof behavior, intercept data, or exploit internal logic.
These threats impact far more than just financial services. Any app with sensitive flows, APIs, or proprietary content is a target. App Shield helps neutralize these risks at runtime without requiring manual intervention or rewriting code.
Real-World Use Cases
- EdTech platforms: Prevent unauthorized cloning of premium content and ensure app integrity on low-trust devices.
- HR and workforce apps: Secure personal and operational data across a wide range of employee-owned devices.
- Mobility and transport services: Defend against location spoofing, fake app repackaging, and runtime manipulation.
App Shield doesn’t just secure your app, it fits into how you already work. Whether you’re pushing daily builds or managing multiple product tracks, you can integrate V-OS App Shield directly into your CI/CD pipeline using our secure API, so every production release is automatically protected, without slowing down your dev flow.
- Flexible integration via portal or API
- Shielded builds in minutes
- Zero changes to app logic or performance
- Invisible at runtime, effective in the wild
With App Shield, protection is built in, so you can keep building fast without sacrificing security.