The rise of mobile apps has completely changed how people live, work, and connect with the world. From banking and shopping to healthcare and entertainment, there’s a mobile app for practically everything. This convenience, however, comes with a growing threat: mobile app data breaches. These breaches can expose sensitive customer information and result in substantial financial losses.
According to the IBM Security’s Cost of a Data Breach Report 2023, the global average cost of a data breach reached a staggering USD 4.45 million. This figure represents a 15% increase over just three years, highlighting the escalating financial burden breaches pose. For an SME, such a financial blow can be catastrophic, potentially leading to bankruptcy or forced closure.
The Stakes Are High: What Can Happen if Your Mobile App Isn’t Secure?
Beyond the immediate financial cost, the consequences of a mobile app data breach can be far-reaching. Here’s a breakdown of the potential risks:
- Financial Loss: Breaches can expose sensitive customer data like credit card details, names, addresses, and even health information. This can lead to financial losses through fraudulent transactions, chargebacks, and hefty fines for non-compliance with data protection regulations like GDPR (General Data Protection Regulation).
- Erosion of User Trust: Consumers are increasingly privacy-conscious and expect businesses to handle their data responsibly. A data breach demonstrates a lack of security and can severely damage user trust in your brand. This can lead to negative reviews, a decline in user engagement, and difficulty acquiring new users.
- Loss of Competitive Advantage: Mobile apps are often a key differentiator for businesses. If your app is compromised by a security breach, it can expose your intellectual property or unique features to competitors, giving them an unfair advantage.
Real-World Examples: A Glimpse into Mobile App Breaches
Here are some real-world examples of how mobile app breaches have impacted:
Grubhub (2021): Grubhub experienced a data breach where customer information, such as email addresses, phone numbers, and delivery addresses, was exposed. While specific details were not disclosed, such breaches often stem from inadequate mobile app security, including insufficient encryption and vulnerabilities in the app’s code.
ApkPure (2021): ApkPure, a popular third-party app store, was found to distribute a version of its app containing malware. The breach involved a malicious code being injected into the ApkPure app. This compromised version of the app was capable of downloading and installing additional malware onto users’ devices without their consent.
These examples highlight the critical importance of mobile app security. Mobile apps lacking in security measures and vulnerable to exploitation are prime targets for attackers.
Mobile App Vulnerabilities: A Sneak Peek into Hacker Tactics
Here are some common methods hackers use to exploit vulnerabilities and compromise your data:
Reverse Engineering: Imagine a hacker peering under the hood of your app, dissecting its code to understand how it works. That’s reverse engineering. By cracking the app’s code, attackers can identify weaknesses and exploit them to gain unauthorized access to sensitive data or even inject malicious code.
Tampering: Think of this as vandalism in the digital world. Hackers might tamper with your app, modifying its code to steal data, redirect users to fake websites that harvest information, or inject intrusive ads. This can not only harm your users’ experience but also damage your brand reputation.
API Exploits: APIs (Application Programming Interfaces) are the behind-the-scenes messengers that connect your app to other services. Hackers can exploit vulnerabilities in these APIs to gain unauthorized access to data or even control app functionality. Imagine a hacker breaking into a bank vault through a weak ventilation system – that’s the idea behind API exploits.
Malware Injection: Hackers can inject malicious software (malware) into your app through various means. Once installed, this malware can steal data, track user activity, or even take control of the device entirely. Imagine a Trojan Horse carrying hidden threats – that’s the concept behind malware injection.
Mitigating the Risk of Mobile App Breaches
Mobile apps are treasure chests of personal information, making them prime targets for cyberattacks. Data breaches can be devastating leading to financial losses, reputational damage, and regulatory fines. Fortunately, there are robust mobile app security solutions that can take to significantly reduce the risk of mobile app breaches and provide an extra layer of protection for your app. These solutions can identify vulnerabilities, detect and prevent attacks, and help you maintain a high level of security.
V-OS App Shield: Fast and Easy Security Solutions for Your Mobile Apps
V-OS App Shield is a cloud-based mobile application security solution designed to protect your app from a wide range of threats, all without requiring any code changes to your existing app. This makes it ideal to seek a straightforward and effective way to safeguard their mobile apps.
Here’s how V-OS App Shield steps in as your trusted partner, offering a robust mobile app security solution to mitigate the risk of breaches.
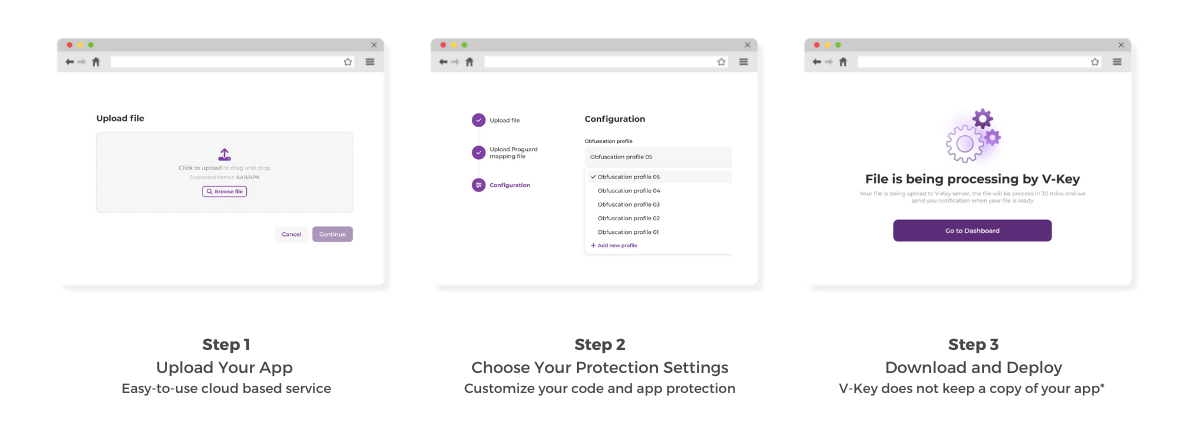
- Effortless Integration: V-OS App Shield offers a no-code integration. Simply follow 3 steps to deploy. It’s that easy!
- Fortifying Your Code: V-OS App Shield employs code obfuscation techniques to make your app’s code more complex and challenging to understand. This significantly hinders attackers’ attempts to reverse engineer your app and identify vulnerabilities.
- Configurable App Protection Profile with OTA Update: Decide how you want your app to respond to each threat category and update it anytime over-the-air to all devices
- Isolation of Security and Crypto Logic: Strong protection for security and crypto logic, just like a hardware secure element or Trusted Execution Environment (TEE)
- Real-Time Threat Intelligence: Cybersecurity threats are constantly evolving. V-OS App Shield leverages real-time threat intelligence to stay ahead of the curve. This allows V-OS App Shield to proactively identify and block malicious activity before it can compromise your app.
- Globally Certified: Certified by 3rd-party evaluation labs using globally-recognized security standards such as FIPS-140 and Common Criteria
Beyond these core features, V-OS App Shield offers additional benefits:
- Reduced Risk of Regulatory Fines: V-OS App Shield’s robust security measures help you meet data protection compliance requirements.
- Improved User Trust and Confidence: By demonstrating a commitment to strong mobile app security, V-OS App Shield helps build trust with users, leading to increased customer satisfaction and loyalty.
- Simplified Security Management: V-OS App Shield offers a centralized management console for easy monitoring and control of your app’s security posture.
V-OS App Shield empowers you to embrace the mobile world with confidence and peace of mind. It provides a multi-layered defense, making your mobile experience safer and more enjoyable.